Why Training Alone is No Longer Enough to Prevent Email Cyber Attacks
The Increasing Sophistication of Email Cyber Attacks
In recent years, malicious emails have evolved dramatically. What was once easily identifiable as suspicious now often appears indistinguishable from legitimate communication, making traditional training and filtering methods increasingly ineffective.
Types of Email Cyber Attacks
Cyber attacks via email come in various forms, with the most common being spam, phishing, and targeted attacks. Spam involves mass unsolicited messages that clutter inboxes. Phishing emails impersonate legitimate organizations to steal personal information using increasingly sophisticated techniques. Targeted attacks are customized messages aimed at specific individuals or organizations, carefully crafted to exploit their targets. These attacks prey on human error, requiring constant vigilance.
Here are the key characteristics of each:
Targeted Attack Emails
- Characteristics: Highly customized content based on extensive research about the recipient’s background and behavior patterns, often impersonating trusted senders.
Phishing Emails
- Characteristics: Typically use general service information rather than targeting specific personal details.
Spam Emails
- Characteristics: Primarily used for advertising and promotional purposes.
Prevention Measures and Their Limitations
Preventing email cyber attacks requires more than just basic filtering and training. Modern attackers can easily spoof legitimate email addresses, making traditional defense measures and training alone insufficient. So, what can be done?
Strategies to Reduce Impact
Given the difficulty of completely preventing email cyber attacks, traditional measures like:
Multi-layered Defense: Implementing multiple security layers including email filtering, firewalls, and antivirus software to minimize potential damage from successful attacks.
Employee Education: Beyond regular training, continuously sharing information about emerging attack methods to maintain high alertness among staff.
…are no longer enough. Consider these additional approaches:
- Incident Response Planning: Develop and maintain a response plan to quickly address and contain damage from successful attacks.
- Network Segmentation: Divide networks and systems into segments to limit the impact of a breach. For example, during the Kadokawa attack, segmented networks helped protect critical data.
These measures can effectively reduce the impact of cyber attacks.
ePrize also faces numerous attacks daily. Here are some examples of the sophisticated emails we receive:
Could you identify these as malicious?
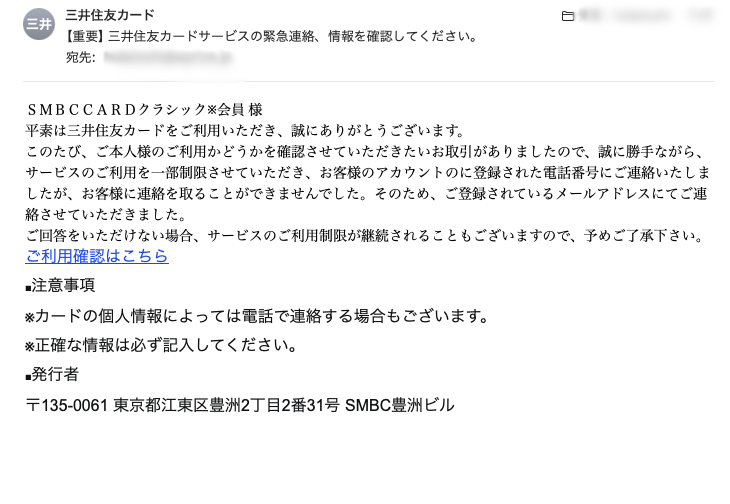
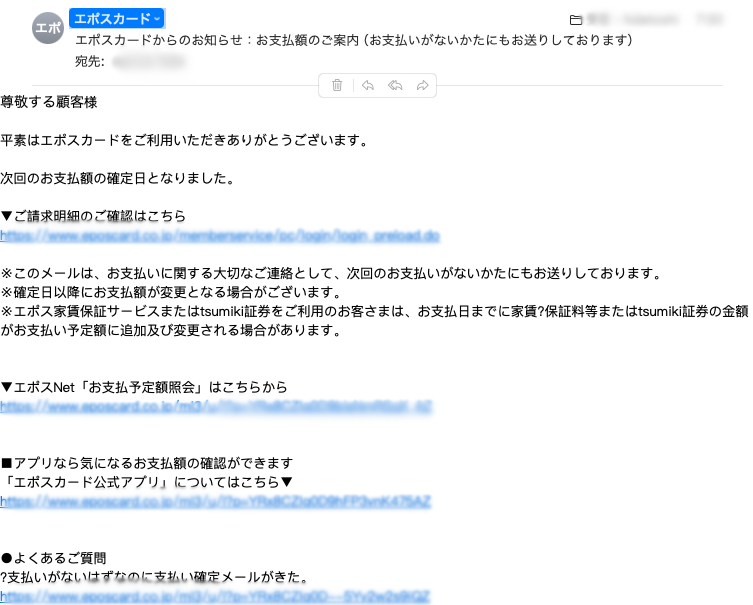
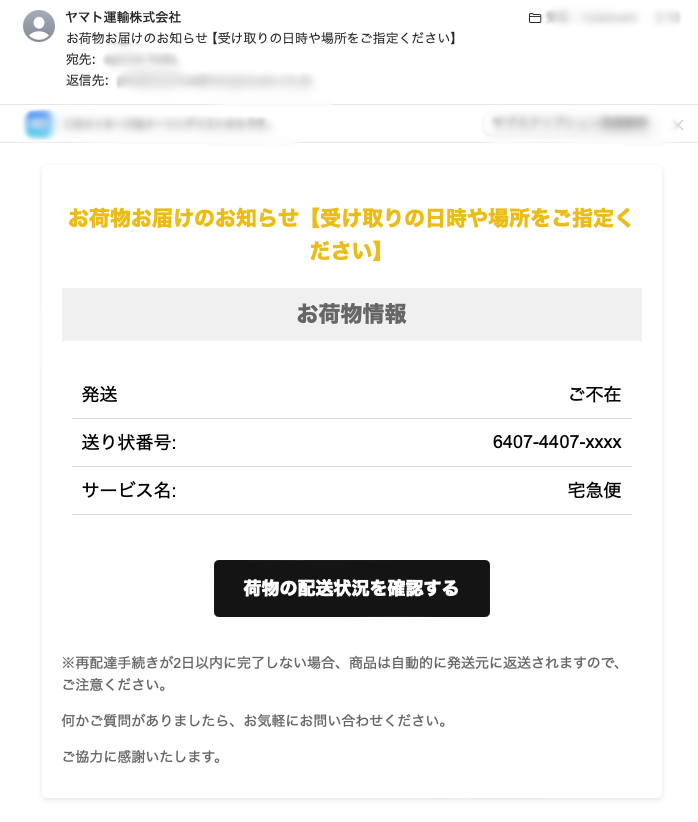
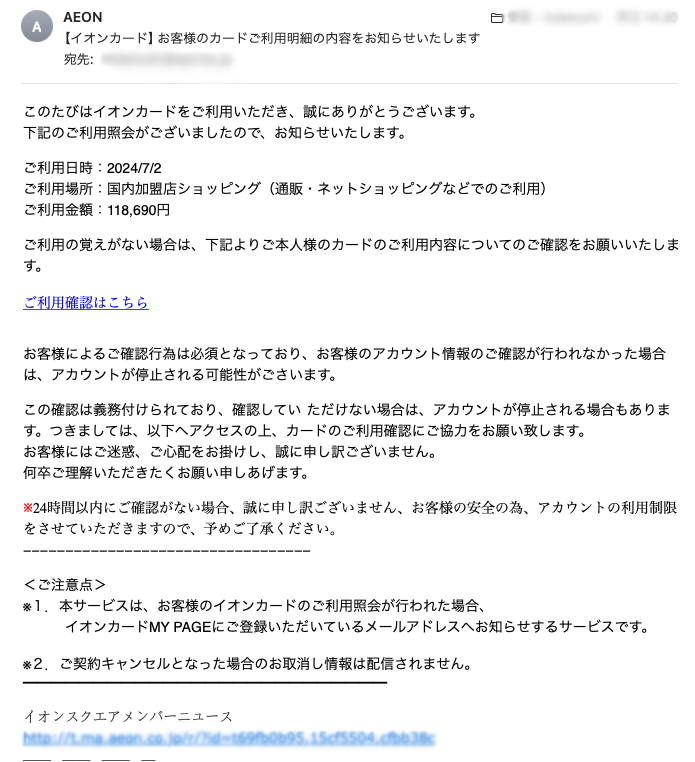
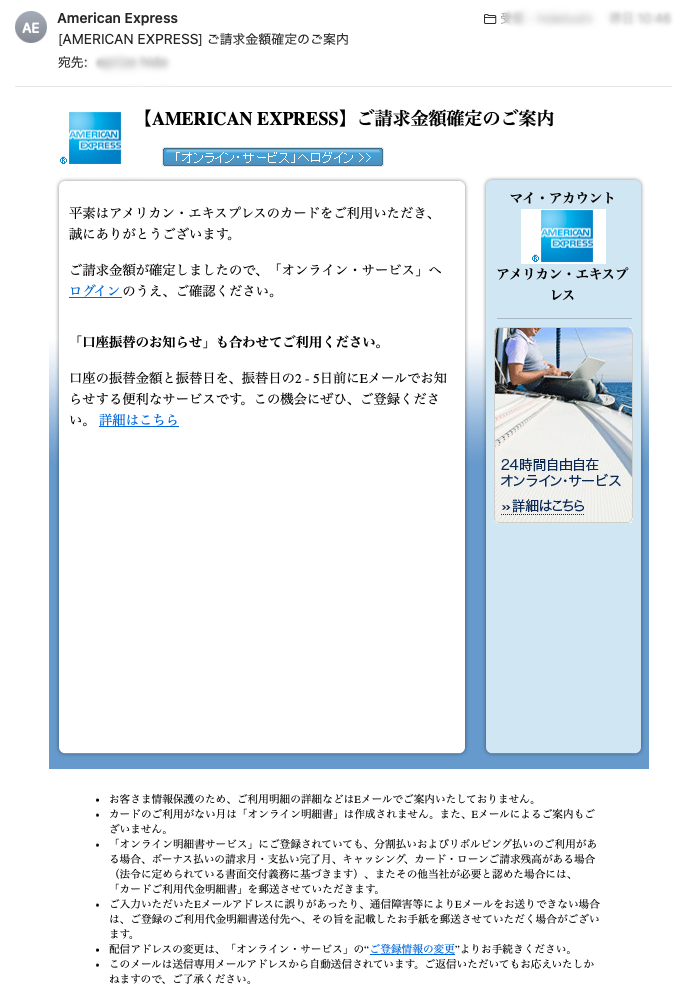
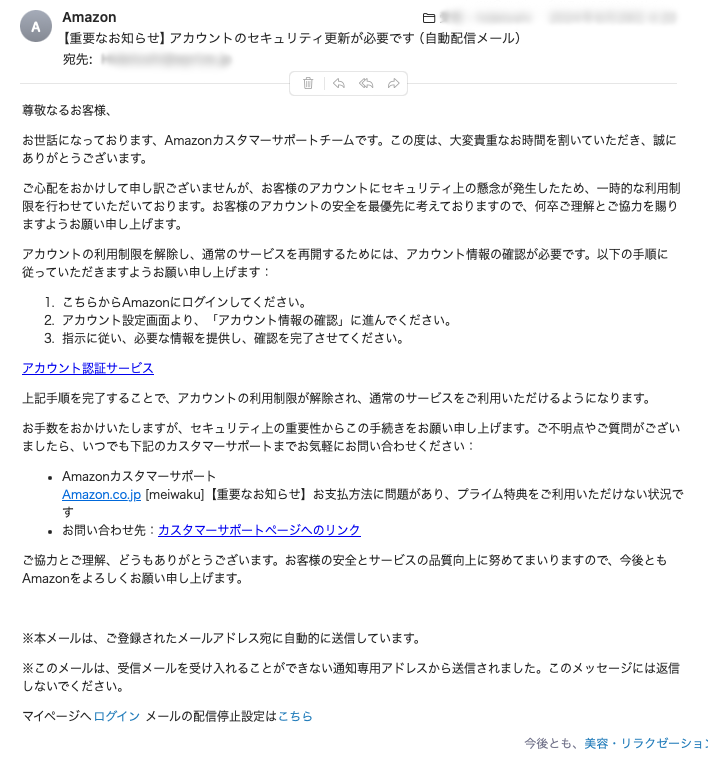
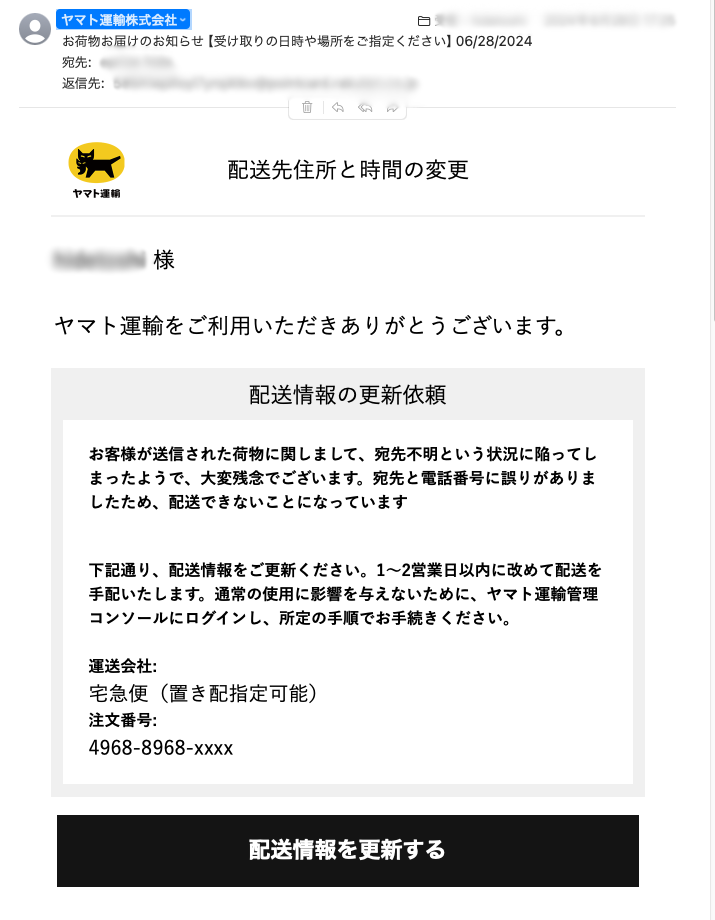
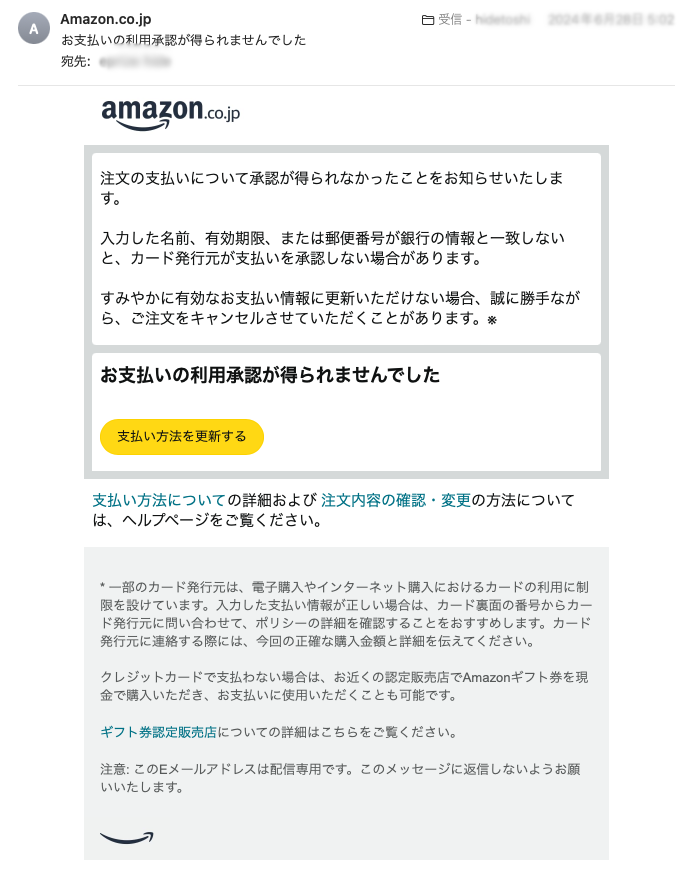
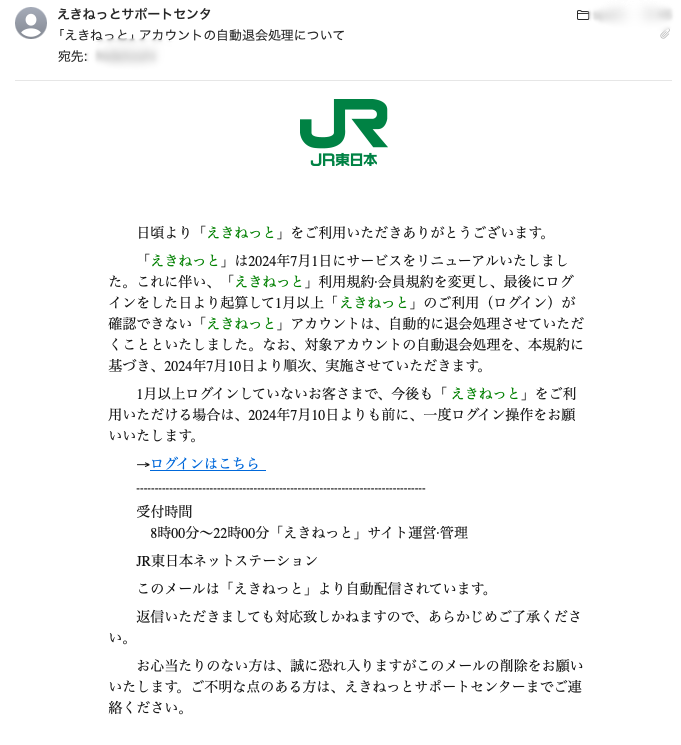
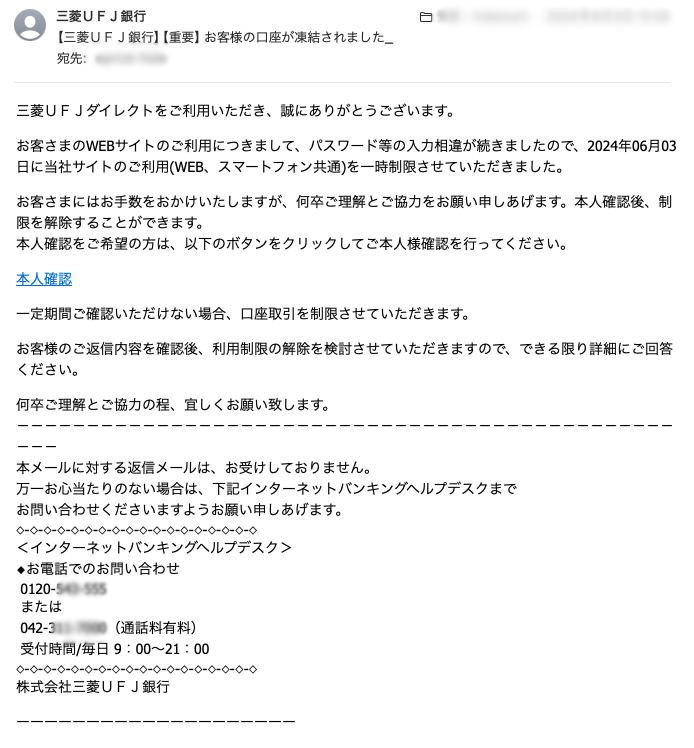
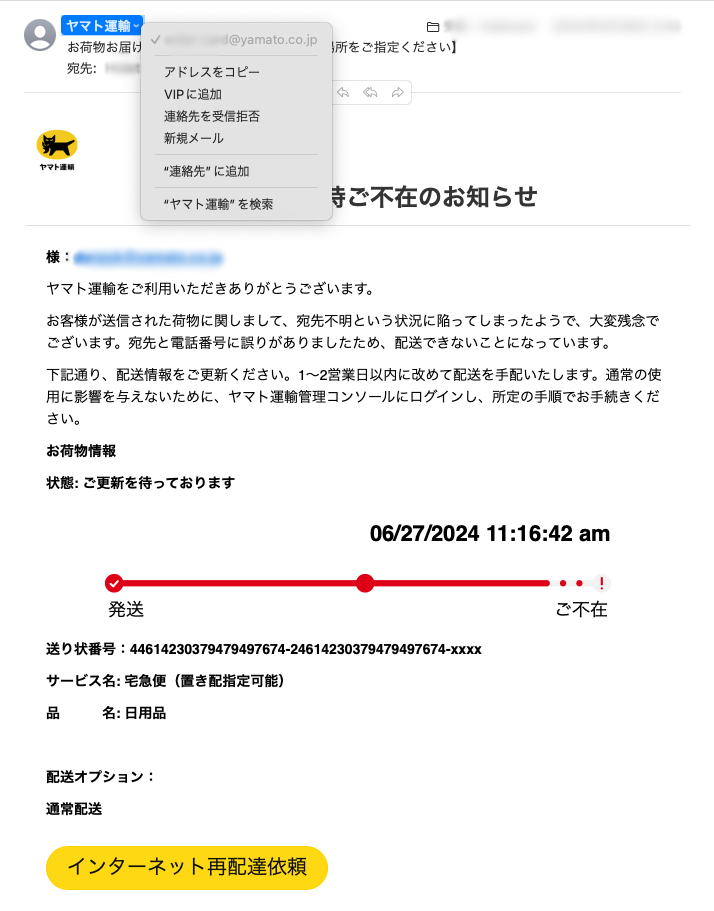
Conclusion
As email-based cyber threats continue to grow in sophistication, traditional defense methods alone are increasingly inadequate. In this environment, multi-layered defense strategies and rapid incident response have become critical. Since completely preventing attacks is often impossible, the focus must shift to minimizing damage—a key challenge in modern organizational security strategies.